In Information Technology, Denial of Service (DoS; English for "refusal of service") refers to the unavailability of an Internet service that should actually be available. [..] This can be caused unintentionally or as a result of a concerted attack on the servers or other components of the data network. — https://wikipedia.org/wiki/Denial_of_Service
DDoS — Not Really a Problem
The provision of professional protection against DDoS attacks is an essential part of our product portfolio. This is no coincidence: As I'm sure some of you know, the fact that we ourselves had been massively affected by DDoS with our freehosting project at that time led to the desire to be able to offer affordable DDoS protection for virtually every end customer. For example, from 2015, when DDoS Protection was generally still considered priceless, we offered the first products with included DDoS Protection. Over the following years, we continued to work our way into the topic and for several years we have been working largely autonomously, i.e. with solutions that we essentially administer ourselves, so that we can make necessary adjustments for our customers at any time without third parties.
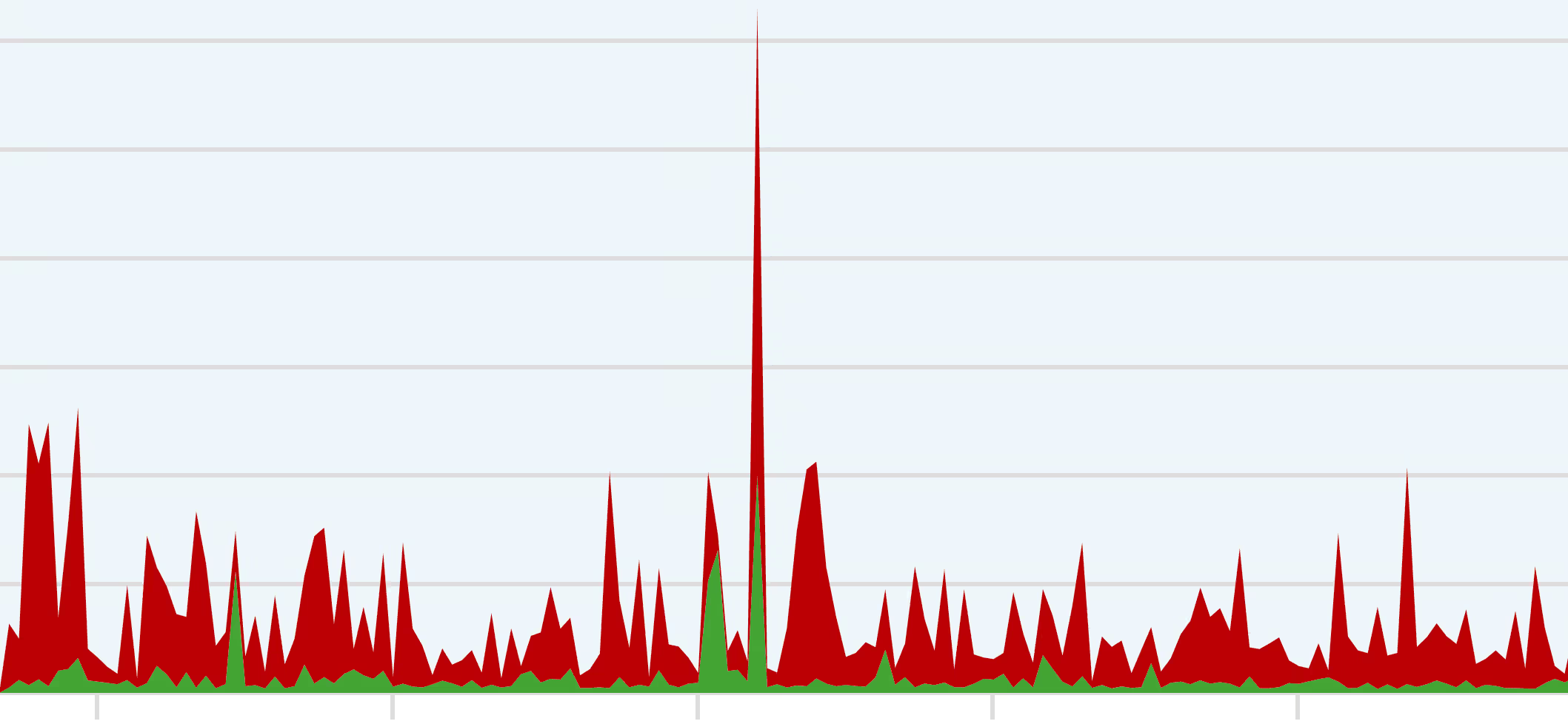
Now it is not uncommon as a DDoS Protection Provider to regularly become a target yourself if an attacker doesn't get their target offline. For example, our own websites are the target of such attacks every week; usually without success. Even so-called carpet bombing attacks are unfortunately completely normal. Instead of a single server, an entire network area (typically 256 IPs) with an immense bandwidth is attacked simultaneously in order to make detection and filtering, which normally applies per IP address, difficult, since the attack bandwidth associated with a single IP address is not significant. But we also counteract such attacks within minutes and usually even fully automatically. It was the same last Sunday (26.03.2023) when hundreds of DDoS alerts suddenly arrived within a few minutes and related to exactly one of our IP networks. The attack was mitigated within a few minutes without significant restrictions and customers remained available.
But..?
However, since the late evening hours of Monday (27.03.2023), we have been receiving a wave of DDoS attacks of a different quality. It will be a variety various Network areas attacked simultaneously. The attacks have never caused a complete failure due to more than sufficient connectivity between our carriers, but have certainly caused packet losses — primarily in the directly affected (attacked) networks. Because of the structure of the attacks, it is more difficult to react to them this time.
Who was (or is) affected?
As is well known, we are a fan of transparent communication, but here we have to balance between comprehensible interest on the customer side and the protection of our network (and therefore all customers). As a result, we decided not to communicate too many details that could benefit the attackers. However, we can say at this stage that around 20% of our IP networks are attacked much more regularly than others and that our label Avoro Vis-à-vis our label PHP-Friends Is significantly more affected, as more gaming services are operated there, which unfortunately are simply the target of DDoS attacks more often. However, because some network areas are also used for both labels, it is not possible to make a general statement. Since the attacks are primarily carried out via UDP, our current (additional) filtering measures also primarily relate to UDP, so that TCP applications have not been affected so far. IPv6 traffic is also completely unaffected by the attacks.
From our point of view, it is particularly important to understand that, on the one hand, only a small proportion of all customers are affected and, on the other hand, there are no complete network failures. Anyone who is affected themselves will probably notice this, and anyone who doesn't notice anything is probably not affected.
Next steps and timetable
With the start of yesterday's carpet bombing attacks, we immediately adapted our filtering measures to the respective attack patterns and continue to do so, around the clock, whenever necessary — in particular with the help of our main carrier. In this way, we were able to keep the damage caused by the bank low and, above all, limited it to a few seconds, even for the affected customers.
In order to be able to carry out more optimal (more granular) filtering of attacks, we ordered additional network equipment via express last night, which will reach our data center tomorrow (29.03.2023) and will then be installed and set up. We expect the situation to be put into operation and therefore likely to resolve the situation on Thursday, 30.03.2023 at the earliest.
Until then, the status quo of making all technically feasible adjustments with the existing equipment remains. During the day, we have refined our filters configured overnight to such an extent that the collateral damage of further attacks is even lower, i.e. affects far fewer customers and is usually in the range of seconds for them. We understand that any packet loss that occurs is still very annoying for affected customers.
It is natural that we do not know whether there will be further attacks today and in the coming days, but we are (and remain) well prepared for the situation.
Thanks
We would like to thank all affected customers for their understanding and assure you that we will continue to work hard around the clock on a stable network. We will update the blog post with new information as soon as possible and are always available to answer your questions on all channels — ticket, email, social media.
Update 29.03.2023
The delivery of network equipment from the Netherlands, which was actually expected today, is currently "hanging" at customs and will therefore only arrive tomorrow. However, we were still able to achieve significant improvements in our filtering measures today, so that the impact of the ongoing attacks was low right from the start of the day, has diminished over the last few hours and is currently zero to the best of our knowledge and belief. Since the first attack — as we did yesterday — we have taken live countermeasures and responded to any adjustment of attack patterns within a few minutes. We are therefore carefully giving the all-clear at this point — the attacks should no longer have an impact on our customers.